IBM CP4BA Importing the certificate of an external service
To integrate with an external service, you must first import its Transport Layer Security (TLS) certificate in Privacy Enhanced Mail (PEM) format into the operator trust list. The certificate is added to the truststore of each component in the Cloud Pak. Source: Importing the certificate of an external service
In summary, the entire path to adding a certificate to IBM Cloud Pak consists of four steps. Below you'll find all the commands and instructions you need to complete this task.
To install the oc commands, visit Getting started with the OpenShift CLI. There, you'll find instructions for installing and configuring the tool, which allows you to control your OpenShift cluster from the local command line.
Download the kubectl command from https://storage.googleapis.com/kubernetes-release/release/v1.23.2/bin/windows/amd64/kubectl.exe and place it in the appropriate directory.
Step 1. Log in to the OpenShift cluster
First, you need to log in to the OpenShift cluster using the oc tool.
oc login https://api.68acab470454c5ff80d0bb37.eu1.techzone.ibm.com:6443 -u <username> -p <password>
where:
<username>is your username (e.g.,kubeadmin)<password>is your password.
Make sure you're working in the correct namespace for IBM Cloud Pak. Set it by issuing the following command:
oc project cp4ba
Step 2. Download the certificate
Download the TLS certificate from the external service you want to integrate with. In this example, we're using the service https://apim.eu.workato.com. Use one of the following methods to download the certificate and save it to a .crt file (in the examples below, the filename is apim-eu-workato-com-cert.crt).
- Use the
keytoolutility to download the certificate chain from the external service and save it to the.crtfile:
keytool -printcert -sslserver https://apim.eu.workato.com -rfc > apim-eu-workato-com-cert.crt
- Use the
opensslutility to download the certificate from the external service and save it to the.crtfile:
echo | \
openssl s_client -showcerts -connect apim.eu.workato.com:443 | \
sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > apim-eu-workato-com-cert.crt
Step 3. Create a Kubernetes Secret
Next, create a Kubernetes Secret to store the certificate. The secret is created in the cp4ba namespace and named apim-eu-workato-com.
kubectl create secret generic apim-eu-workato-com --from-file=tls.crt=apim-eu-workato-com-cert.crt -n cp4ba
Step 4. Update the Cloud Pak Configuration
The final step is to update the YAML file in the OpenShift console so that the deployment uses the newly created secret.
- Log in to the OpenShift console.
- Go to Operators > Installed Operators and click IBM Cloud Pak for Business Automation.
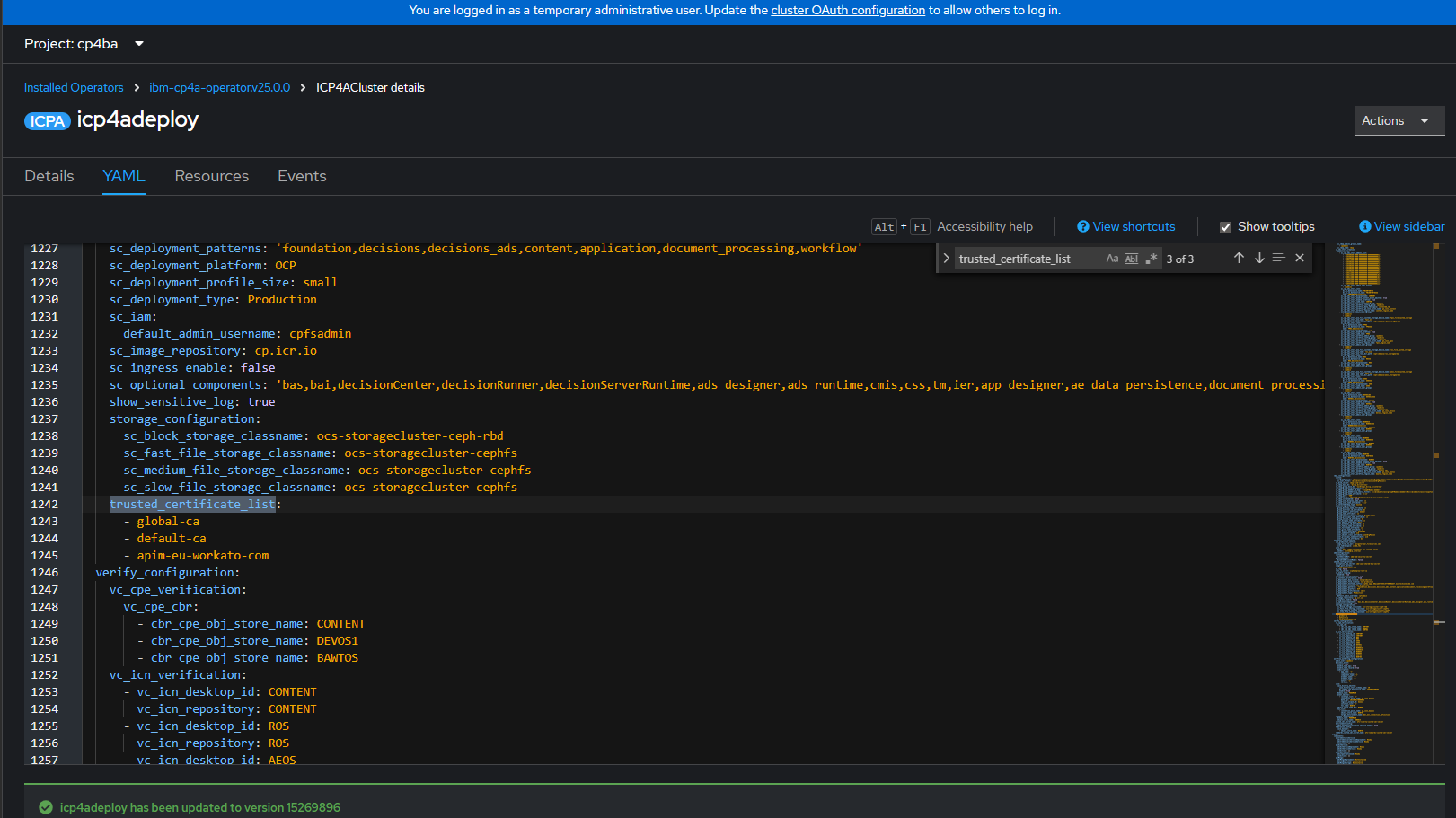
- Go to the deployment tab, usually icp4adeploy, and select YAML.
- In the YAML file, locate the 'shared_configuration' section and add your secret name (
apim-eu-workato-com) to the 'trusted_certificate_list`.# ...
spec:
shared_configuration:
trusted_certificate_list:
- apim-eu-workato-com
# ... - Save your changes. The operator will automatically update the deployment so that components can trust the new certificate.
Make sure the configuration is saved. Sometimes, the OpenShift console doesn't save changes to the YAML file. This is because the YAML tab also contains status data for some pods, and this data can change. This is annoying, but you have to accept it. In this case, reload the configuration (the Reload button) and try making changes again.